
Given the rapid growth of cryptocurrencies in popularity and usage, ensuring security has become essential. With digital assets reaching exceptional values, finding secure storage solutions is more critical than ever. Hardware wallets have emerged as a favored choice, with Ledger emerging as a prominent player in this domain.
However, despite their widespread adoption, lingering questions persist about the security of Ledger hardware wallets.
In this article, we will carefully examine the safety features of Ledger’s hardware wallets and assess their overall level of security.
What Is a Hardware Wallet?
Table of Contents
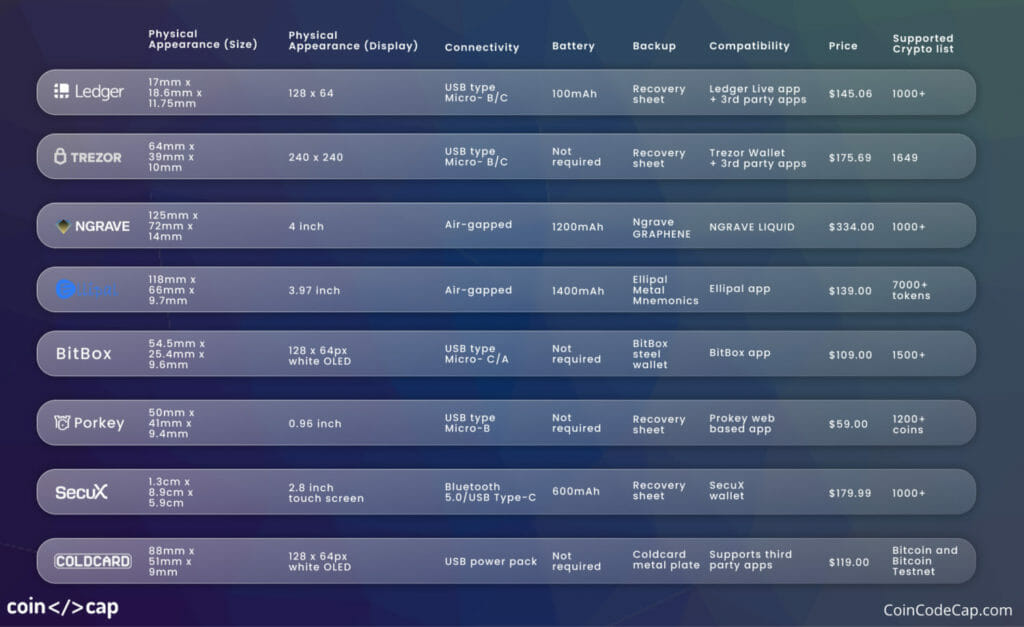
Source: Coin Code Cap
When it comes to self-custody of your digital assets, taking every possible measure to protect your holdings is of utmost importance. And one highly recommended method for storing and securing your coins is using hardware wallets.
But what exactly is a hardware wallet?
Hardware wallets are physical devices that often resemble USB sticks and operate as simplified single-purpose computers.
It serves as a secure storage for private keys by storing them offline or in “cold” storage – meaning they are not connected to the internet unless temporarily linked to a computer for transaction purposes.
On the other hand, software- or web-based crypto wallets (“hot” wallets) remain permanently online, thereby increasing the potential attack vectors for hackers to exploit and drain your funds.
The offline nature of hardware wallets considerably reduces the risk of unauthorized interferences and resultant thefts. The private keys remain secure even if the user links a hardware wallet to a compromised computer or device.
Consequently, a hardware wallet is an exceptionally safe choice for safeguarding crypto assets, effectively keeping them beyond the reach of unauthorized individuals.
Ledger Hardware Wallets

Ledger, a renowned industry leader, boasts a remarkable track record of nearly a decade in manufacturing hardware cryptocurrency wallets.
Presently, Ledger offers a diverse range of three exceptional hardware wallets: the interactive Stax, the mobile-ready Nano X, and the cost-effective Ledger Nano S Plus. These hardware wallets seamlessly integrate with Ledger Live, an impressively feature-rich application that enhances the overall user experience.
With Ledger’s cutting-edge hardware wallets and the power of Ledger Live, users can access a comprehensive suite of tools and functionalities to manage their digital assets securely.
How Secure Are Ledger Wallets?
Robust Security Framework with Secure Element (SE)
A crucial element that underpins the security of Ledger hardware wallets is its robust security framework. At the heart of this framework lies a secure chip called the Secure Element (SE), renowned for its impregnability against sophisticated attacks and its ability to safeguard the integrity of private keys.
The Secure Element is a chip commonly employed in high-security applications such as passports and credit cards, where stringent safety measures are paramount. Its tamper-resistant nature allows it to securely store and execute cryptographic operations, rendering it highly resistant to physical and software-based attacks.
Hierarchical Deterministic (HD) Wallet Structure
In addition, Ledger hardware wallets implement a hierarchical deterministic (HD) wallet structure, which offers significant advantages. This structure entails using a single seed phrase to generate multiple private keys.
Users create a seed phrase (a password-like collection of random words) during the initial setup process. This approach eliminates the need for individual key backups, simplifying the backup procedure.
Furthermore, the seed phrase acts as a failsafe, granting access to the wallet in case of device loss or damage. Ledger devices offer users a 12- to 24-word seed phrase, offering an extensive range of combinations.
This scenario makes it exceedingly challenging for attackers to guess or employ brute-force methods to crack the phrase, thereby minimizing the risk of external attacks.
Secure User Experience with Ledger Live
Ledger also offers a secure user experience through its proprietary software, Ledger Live. This software serves as a gateway to manage cryptocurrencies stored on Ledger devices. Ledger Live operates on the principle of end-to-end encryption, ensuring that sensitive data such as private keys or recovery phrases are securely transmitted and stored on the user’s computer.
Additionally, Ledger Live verifies the integrity of firmware updates before installation, safeguarding against malicious software modifications.
Integrated Displays for Transaction Verification
To further enhance security, Ledger hardware wallets have integrated displays. These displays allow users to verify and confirm transaction details directly on the device, minimizing the risk of malicious actors intercepting or altering transaction information. Users can visually confirm the transaction amount, recipient address, and fees before approving the transaction, adding an extra layer of protection against fraudulent activities.
Rigorous Security Testing and Auditing
Another noteworthy aspect is the rigorous security testing and auditing performed on Ledger’s products. The company regularly conducts thorough security assessments, including penetration testing and vulnerability assessments, to identify and mitigate potential vulnerabilities.
Moreover, independent security researchers and auditors scrutinize Ledger’s hardware and software for potential weaknesses. This commitment to transparency and proactive security measures helps ensure that Ledger hardware wallets remain at the forefront of secure cryptocurrency storage solutions.
Dedicated Support and Updates via Ledger Support
Finally, Ledger has a dedicated page on Twitter, Ledger Support, to address any security-related concerns and provide ongoing support to users. This page regularly shares the most up-to-date information, including critical updates and scam alerts, to keep users informed and protected.
Where to buy Ledger Hardware
To eliminate risks of counterfeit or tampered devices, the users are advised to purchase Ledger hardware wallets directly from the official website or authorized resellers. The device is alsoavailable on Etherbit, Amazon, Flipkart, etc.
Source: Amazon.com
Possible Threats Ledger Faces
Physical theft
As Ledger is a tangible medium it is vulnerable to physical theft if it goes into the wrong hands. This is possible when the device is lost, stolen, and accessed without authorization. The best recovery measure for this is to built-in a strong security feature that requires the user to enter a PIN code to allow access to the wallet. Users should always keep their PIN code confidential and avoid storing it anywhere near the device. In case of theft or loss, the wallet’s funds can be recovered by using the recovery phrase (the seed phrases) provided during the initial setup of the device. If difficult to remember, these words should be written down and kept in a secure place, preferably offline.
Malware and phishing attacks
As the internet grows, many uninvited external interventions are intruding into our digital boundaries. One such example is hackers using malware or phishing scams to target Ledger wallets. The malware is used in an attempt to compromise the mobile or computer device connected to the wallet, while phishing attacks try to trick users into revealing their wallet credentials. To safeguard your device from tricksters, ensure that the personal devices used to access the Ledger wallet are secure and malware-free.
Moreover, users must update their operating systems and antivirus software on a regular basis to prevent these interventions. Additionally, a user should be cautious not to click on suspicious links or disclose sensitive information in response to unsolicited requests. To ensure increased safety, Ledger has also introduced an addition called an “anti-tampering seal” on its devices to detect any physical interference or unauthorized opening.
Supply chain attacks
A supply chain is central for the manufacturing and distribution of Ledger wallets, which makes the device prone to attackers. Malicious actors could compromise the devices during production or distribution, potentially introducing vulnerabilities or backdoors. To avert this Ledger had employed a variety of security measures, including secure elements and cryptographic checks, to mitigate the risk of supply chain attacks. There are also methods where a user can cross-check the reliability of their device by examining the security seal and visiting Ledger’s official website to validate the legitimacy of the device.
No security system is entirely foolproof. While Ledger hardware wallets have an excellent track record, they are not immune to potential risks. A potential vulnerability comes in the manufacturing and distribution side which is the supply chain attack. To mitigate this threat, Ledger has implemented strict supply chain security measures, including cryptographic attestation and verification of the device’s authenticity.
Above all the technological defenses, the sole responsibility of safety is in the hands of the wallet user. So DYOR and be safe out there!
Found value in the insights shared here? Check out our YouTube and Twitter, loaded with content meant to educate and entertain.
Follow our Telegram for a sneak peek at alpha; for an even deeper dive, join our Patreon community, where we share exclusive alpha for you to be the ‘early bird.’
Follow us today, and let’s explore Web3 together!












